Transmission Control Protocol
- The transmission Control Protocol (TCP) is one of the most important protocols of Internet Protocols suite.
- It is most widely used protocol for data transmission in communication network such as internet.
Features of TCP
- TCP is reliable protocol.
- That is, the receiver always sends either positive or negative acknowledgement about the data packet to the sender, so that the sender always has bright clue about whether the data packet is reached the destination or it needs to resend it.
- TCP ensures that the data reaches intended destination in the same order it was sent.
- TCP is connection oriented.
- TCP requires that connection between two remote points be established before sending actual data.
- TCP provides error-checking and recovery mechanism.
- TCP provides end-to-end communication.
- TCP provides flow control and quality of service.
- TCP operates in Client/Server point-to-point mode.
- TCP provides full duplex server, i.e. it can perform roles of both receiver and sender.
TCP Header
- The length of TCP header is minimum 20 bytes long and maximum 60 bytes.
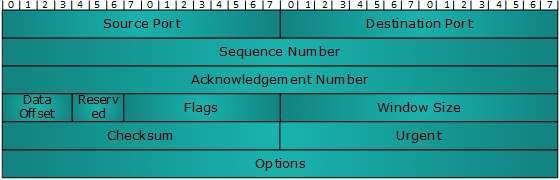
Source Port (16-bits) -
- It identifies source port of the application process on the sending device.
Destination Port (16-bits) -
- It identifies destination port of the application process on the receiving device.
Sequence Number (32-bits) -
- Sequence number of data bytes of a segment in a session.
Acknowledgement Number (32-bits)
- When ACK flag is set, this number contains the next sequence number of the data byte expected and works as acknowledgement of the previous data received.
Data Offset (4-bits)
- This field implies both, the size of TCP header (32-bit words) and the offset of data in current packet in the whole TCP segment.
Reserved (3-bits)
- Reserved for future use and all are set zero by default.
Flags (1-bit each) -
NS - Nonce Sum bit is used by Explicit Congestion Notification signaling process.
CWR - When a host receives packet with ECE bit set, it sets Congestion Windows Reduced to acknowledge that ECE received.
ECE -It has two meanings
- If SYN bit is clear to 0, then ECE means that the IP packet has its CE (congestion experience) bit set.
- If SYN bit is set to 1, ECE means that the device is ECT capable.
- URG - It indicates that Urgent Pointer field has significant data and should be processed.
- ACK - It indicates that Acknowledgement field has significance. If ACK is cleared to 0, it indicates that packet does not contain any acknowledgement.
- PSH - When set, it is a request to the receiving station to PUSH data (as soon as it comes) to the receiving application without buffering it.
RST - Reset flag has the following features:
- It is used to refuse an incoming connection.
- It is used to reject a segment.
- It is used to restart a connection.
SYN - This flag is used to set up a connection between hosts.
FIN - This flag is used to release a connection and no more data is exchanged thereafter. Because packets with SYN and FIN flags have sequence numbers, they are processed in correct order.
Windows Size - This field is used for flow control between two stations and indicates the amount of buffer (in bytes) the receiver has allocated for a segment, i.e. how much data is the receiver expecting.
Checksum - This field contains the checksum of Header, Data and Pseudo Headers.
Urgent Pointer - It points to the urgent data byte if URG flag is set to 1.
Options - It facilitates additional options which are not covered by the regular header. Option field is always described in 32-bit words. If this field contains data less than 32-bit, padding is used to cover the remaining bits to reach 32-bit boundary.
Congestion Control
- When large amount of data is fed to system which is not capable of handling it, congestion occurs. TCP controls congestion by means of Window mechanism.
- TCP sets a window size telling the other end how much data segment to send. TCP may use three algorithms for congestion control
- Additive increase, Multiplicative Decrease
- Slow Start
- Timeout React
Timer Management
- TCP uses different types of timer to control and management various tasks:
Keep-alive timer:
- This timer is used to check the integrity and validity of a connection.
- When keep-alive time expires, the host sends a probe to check if the connection still exists.
Re-transmission timer
- This timer maintains stateful session of data sent.
- If the acknowledgement of sent data does not receive within the re-transmission time, the data segment is sent again.
Persist timer:
- TCP session can be paused by either host by sending Window Size 0.
- To resume the session a host needs to send Window Size with some larger value.
- If this segment never reaches the other end, both ends may wait for each other for infinite time.
- When the Persist timer expires, the host re-sends its window size to let the other end know.
- Persist Timer helps avoid deadlocks in communication.
Timed-Wait:
- After releasing a connection, either of the hosts waits for a Timed-Wait time to terminate the connection completely.
- This is in order to make sure that the other end has received the acknowledgement of its connection termination request.
- Timed-out can be a maximum of 240 seconds (4 minutes).









Great article! I have been looking for a reliable tool to improve my Roblox gameplay, and I found rbx fps unlocker really helpful. It boosted my frame rates and made the game run much smoother. Highly recommend it to anyone struggling with low FPS in Roblox!
ReplyDelete